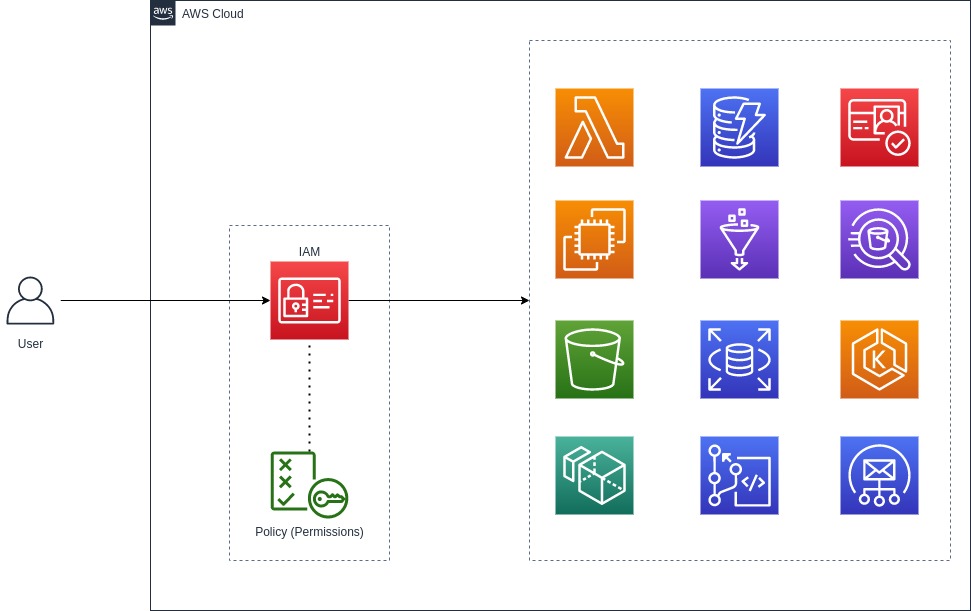
Identity and Access Management (IAM) offers role-based accessed control (RBAC) to your AWS account users and resources, you can granularize the permission set by defining policy. If you are familiar or even a beginner with AWS cloud, you know that how important IAM is. AWS Identity and Access Management (IAM) is a web service that […]